
AMSTERDAM,Sept. 19,2024 -- Group-IB,a leading creator of cybersecurity technologies to investigate,prevent,and fight digital crime,announced today that it has contributed a international operation code named "Operation Kaerb" coordinated by Europol and Ameripol–in partnership with European and Latin American law enforcement agencies and judiciary authorities–which resulted in the arrest of 17 cybercriminals in Argentina,Chile,Colombia,Ecuador,Peru,and Spain,who were behind the iServer phishing-as-a-platform targeting mobile users worldwide. The iServer phishing-as-a-service platform,which was active for five years,is reported by law enforcement investigators to have targeted over 1.2-million mobile phones,and claimed approximately 483,000 victims worldwide. The administrator of the iServer phishing platform,an Argentinian national,was also arrested during the multi-agency law enforcement operation that took place between 10 to 17 September 2024.

iServer's domain seized by local and internal law enforcement agencies
Screenshot of iServer’s website prior to its seizure
Active for at least five years,the iServer platform was primarily used by Spanish-speaking criminals in North and South America,but it has since expanded its reach into Europe and other regions. While iServer was essentially an automated phishing platform,its specific focus on harvesting credentials to unlock stolen phones set it apart from typical phishing-as-a-service offerings. iServer's platform features a web interface that enables low-skilled criminals,known as "unlockers," to steal device passwords,user credentials from cloud-based mobile platforms and other personal information from victims. This allows them to bypass "Lost Mode" and unlock phones acquired through illegal means.
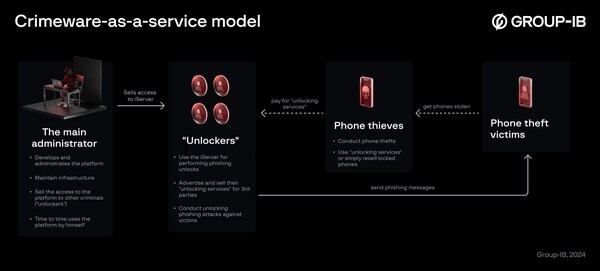
Crimeware-as-a-service model
During its investigations intoiServer's criminal activities,Group-IB specialists also uncovered the structure and roles of criminal syndicates operating with the platform: the platform's owner/developer sells access to "unlockers," who in their turn provide phone unlocking services to other criminals with locked stolen devices. The phishing attacks are specifically designed to gather data that grants access to physical mobile devices,enabling criminals to acquire users' credentials and local device passwords to unlock devices or unlink them from their owners. iServer automates the creation and delivery of phishing pages that imitate popular cloud-based mobile platforms,featuring several unique implementations that enhance its effectiveness as a cybercrime tool.
Unlockers obtain the necessary information for unlocking the mobile phones,such as IMEI,language,owner details,and contact information,often accessed through lost mode or via cloud-based mobile platforms. They utilize phishing domains provided by iServer or create their own to set up a phishing attack. After selecting an attack scenario,iServer creates a phishing page and sends an SMS with a malicious link to the victim.
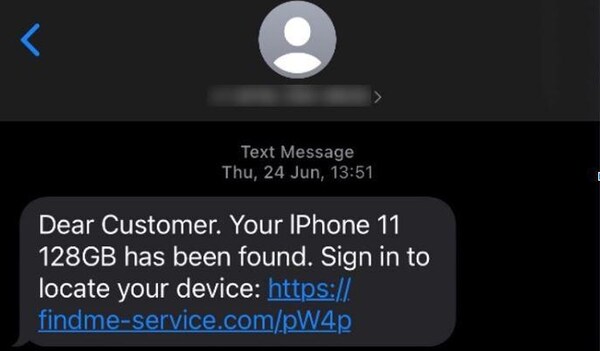
Screenshot of a message received by a victim
A "redirector" link is used to filter and verify the visitor before leading them to the final phishing page; if they do not comply with the rules,access is denied. Once victims enter their credentials,these are verified by the platform,and additional information like OTP codes may be requested.
Screenshot of iServer’s phishing page disguised as a popular cloud-based mobile service website.
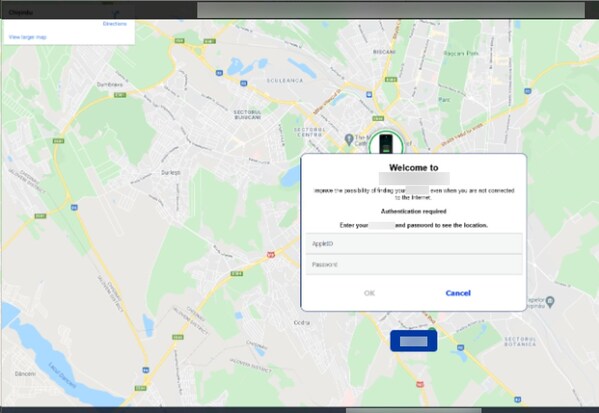
Another example of iServer’s phishing page disguised as a popular cloud-based mobile service website.
Ultimately,criminals receive the stolen and validated credentials through the iServer web interface,enabling them to unlock a phone,turn off "Lost mode" and untie it from the owner's account.
"We are honored to stop millions of cyber attacks targeting mobile users. The arrest of the syndicate members,including the mastermind,has averted significant fraud and safeguarded the personal lives of individuals across various regions," said Dmitry Volkov,CEO of Group-IB. "This serves as yet another great example of cross border collaboration,and we will continue to support local and international law enforcement efforts to combat cybercrime globally."
ABOUT GROUP-IB
Established in 2003,Group-IB is a leading creator of cybersecurity technologies to investigate,and fight digital crime globally. Headquartered in Singapore,and with Digital Crime Resistance Centers in the Middle East and Africa,Europe,Central Asia,and the Asia-Pacific,Group-IB analyses and neutralizes regional and country-specific cyber threats via its Unified Risk Platform,offering unparalleled defence through its industry-leading Threat Intelligence,Fraud Protection,Digital Risk Protection,Managed Extended Detection and Response (XDR),Business Email Protection,and External Attack Surface Managementsolutions,catering to government,retail,healthcare,gaming,financial sectors,and beyond. Group-IB collaborates with international law enforcement agencies like INTERPOL,EUROPOL,and AFRIPOL to fortify cybersecurity worldwide,and has been awarded by advisory agencies including Aite-Novarica,Gartner,Forrester,Frost & Sullivan,and KuppingerCole.
For more information,visit us at www.group-ib.comor connectwith us on LinkedIn,X,Facebook,and Instagram.
FOR MEDIA INQUIRIES
Group-IB Public Relations
PR@Group-IB.com